NICKS V2 - 2019
In late 2019, inspired by the platform conversations I’d had with some of the Democrats in my district I started working on NICKS again. I didn’t want to repeat the mistakes I made last time so I stopped trying to make a phone app and focused on building a core library that I could re-use anywhere.
The second version of NICKS was more successful. The crypto layer came together quickly (since I’d written most of the same logic before) and I was able to quickly stand up a transaction flow:
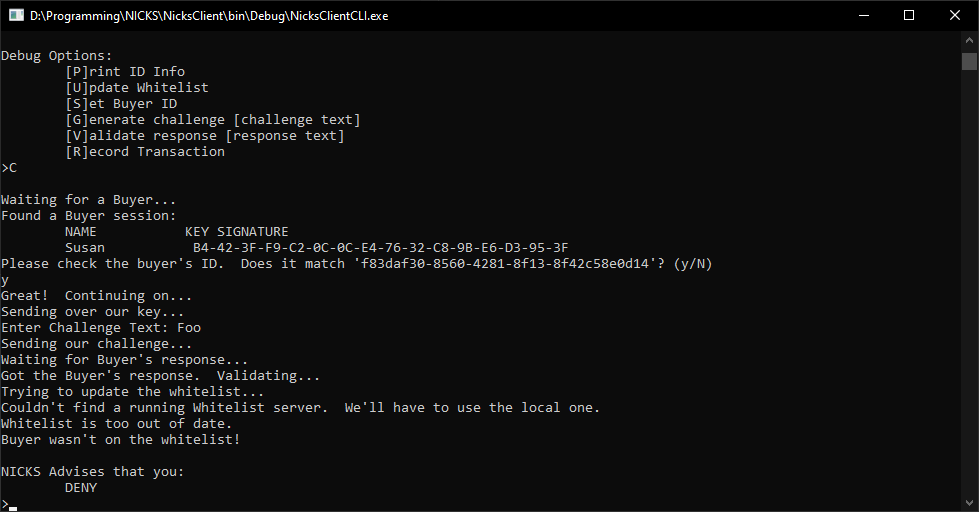
I made two big improvements over V1:
- I actually built the allow-list service that let me check whether users were valid purchasers.
- I created a way to generate transaction records that could be validated later
The allow-list ended up being just a lookup table for public key fingerprints. This sort-of violated goal #4 of NICKS: The allow-list must not include names, such that Proceed / Do Not Proceed information cannot be obtained about Bob without Bob’s permission.. While it was technically true that you couldn’t look up Bob without knowing his public key, security through obscurity isn’t a great approach - especially since public keys are are supposed to be information it’s safe to share publicly.
The transaction records were the real breakthrough here. Being able to generate records of the sale that show a seller performed all the required steps is hugely important for making this system legally viable.
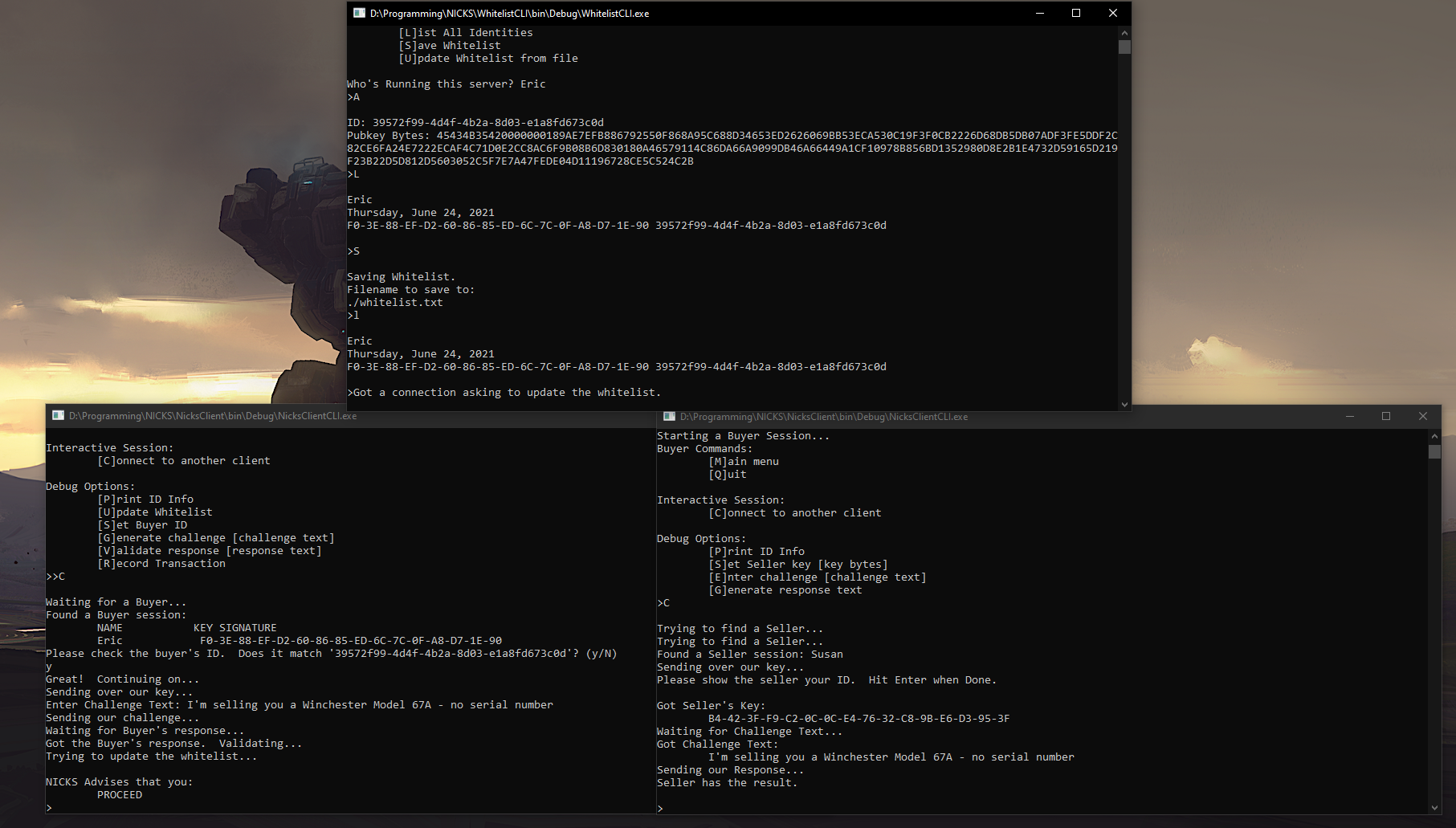
This still had a long way to go before it was viable, but this is the first time I had a demo I could show people. Unfortunately command-line applications aren’t as sexy as they used to be, so the demo fell pretty flat for most people. It turns out to be tough to communicate exactly what’s going on with the crypto that’s happening behind the scenes.